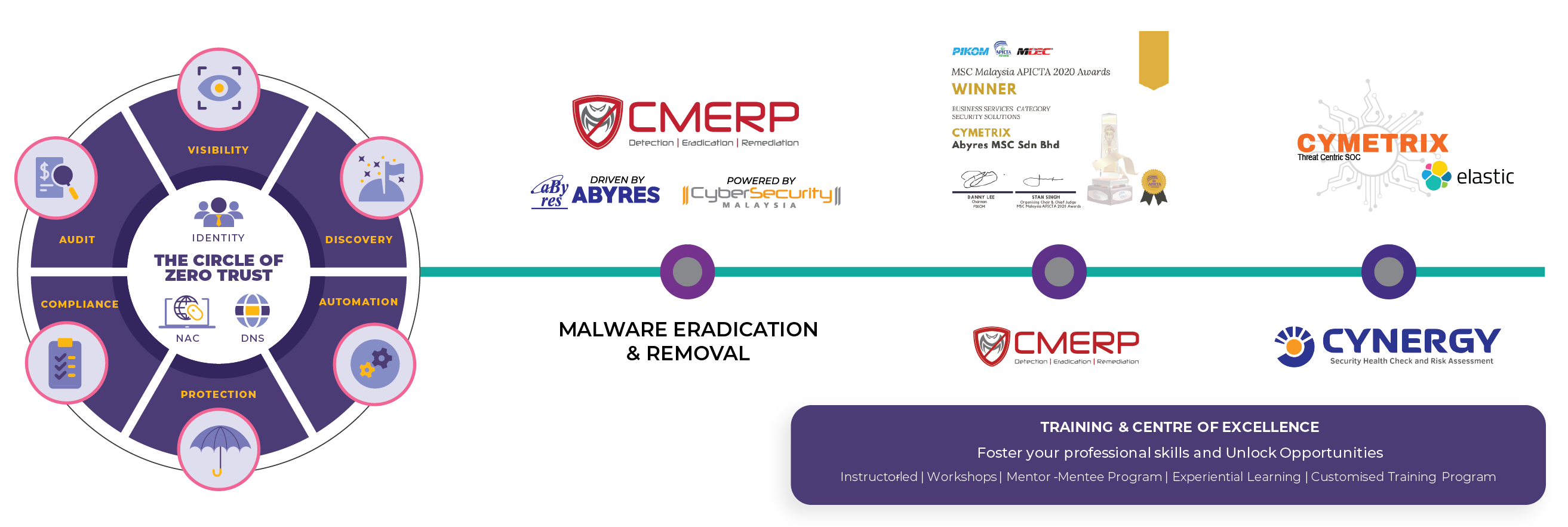
The rapid increase of sophisticated and multifaceted cyber-attacks such as malware attacks and the risk of
consequential damage has ushered in a new age for security solutions. Chief information security officer (CISO)
and Security leaders need advanced threat detection and response tools to enable their organization to discover
and prevent more evasive threats and efficiently resolve security alerts.
The data protection market is
evolving rapidly to address new challenges in regards to exponential data growth, rapid digitalization and
globalization of business, and data privacy. Effective Data backup and recovery solutions will help
organizations to recover from the impact of user errors, application errors, malicious attacks and disaster
events.
JOURNEY